Table of Contents
- Introduction
- System Design
- Design of Copyright Policy Management System
- Design of Policy Enforcement System
- Implementation
- Evaluation
- Conclusion
- Reference
1. Introduction
Copyright management is a most important issue in distributing digital contents over the Internet today. Especially for commercial entity, it is strongly required to strictly control the usage of contents such as www pages, video images, and computer programs. To meet such demand, this paper proposes a practical usage control system based on copyright.In this section, we describe the overview of our system and each component is described in the following sections.
1.1 Goal
The goal of this system is to achieve an environment where- Copyright holder can set copyright policy to every content on the Internet
- Usage of contents is controlled based on copyright policy and user capability
1.2 Main Functions
Main functions achieved by this system are the followings.- 1) Execution of copyright policy
- Copyright policy can be interpreted by program and usage is controlled
in accordance with this policy.
- Copyright policy can be translated to any language and expressed to
users. Users also can check copyright policy at any time and from any place
in the world.
- Users can verify copyright policy set on the contents with digital
signature.
- Authentication of user and verification of capability are required
for users to be authorized.
- Unauthorized use of contents is prevented by distributing contents
with encryption.
1.3 Evaluation
In order to evaluate this system, we adapted this system to an online distance learning system which has over 3,000 students on the Internet, and try to manage various kinds of copyright requirement for various kinds of education materials.This result proves that this
system offers a general usage control system based on copyright on the
Internet.
2. System Design
In this section, we describe the design of "Copyright policy management and enforcement system". We define requirements to achieve the goals listed in 1.1 and describe functions and overview of this system.2.1 Players
There are three kinds of players in this system. Players and their roles are as following.-
1. Copyright Holder - have copyright on contents and set
copyright policy for particular contents
2. Users - use contents under the control based on copyright policy and "capability" the users own
3. Brokers - authenticate users or verify users' rights and issue capability to users
2.2 Requirements
In order to achieve the goal in 1.1, we defined requirements for this system as follows;- Copyright holders can describe their copyright policies and set them to specific contents.
- Copyright policy can be interpreted by system and system can control usage of content based on the policy.
- Copyright holders can compel users to check the policy and require their agreement with it.
- Users are authorized by authentication and check of the capability.
- Tampering of copyright policy and unauthorized use of contents are prevented.
2.3 Design
Usage should be controlled based on copyright policy. Feasibility, reliability and effectiveness are necessary in the design of this system. To achieve this, we devided our system into "Copyright Policy Management System" and "Policy Enforcement System" and designed each component. Details are described in following two sections.Copyright Policy Management System provides a mechanism to set copyright policy to every object on the Internet. This system also assists copyright holders to create copyright policy in intermediate format, which can be interpreted by programs and be translated to any language. This copyright policy is supposed to be widely distributed. Therefore this system uses a protocol designed for copyright policy transaction to manage policy data in a scalable manner. Content data is defined as a set of content ID, copyright policy data with digital signature and encrypted content. The data structure is described in Figure1.
Policy Enforcement System provides a mechanism to control usage based on copyright policy and capability of users. It interprets copyright policy attached to contents, authenticates users and checks the users capability. When all requirements are met, this system decrypts contents and displays them to users.
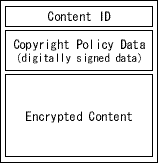
Figure1 : Data Structure
Figure2 shows the whole structure composed of the above two components. As there are several choices in contents placement on contents server, we just show examples in this figure.
Figure2 : System Overview
3. Design of Copyright Policy Management System
In this section, we describe a design of Copyright Policy Management System.We define specification of description language and protocol for copyright policy management in 3.1 and 3.2. In 3.3, functions of each component and operational flow are explained with figure
3.1 Copyright Policy Description Language (CDL)
Copyright Policy Description language (CDL) is designed to describe copyright policy in a intermediate format so that;- Programs can interpret copyright policy
- Copyright policy can be translated into any languages
Syntax of this language is item names and values combined with "=". Item names are single words such as "copy" or "perform" and values are pre-defined numbers and text. A sample is shown in Table1 in section 6.
3.2 Copyright Policy Transfer Protocol (CTP)
In order to manage widely distributed copyright policy in a scalable manner, we designed Copyright Policy Transfer Protocol (CTP). This protocol identifies copyright policy by contents URI and defines the way of registration and retrieval of copyright policy.This protocol uses command and status responses. Commands consist of a command word, which in some cases may be followed by a subcommand word or parameter. There are five kinds of commands words: "HELLO", "VERSION", "REGISTER", "RETRIEVE" and "SERVER". Status response begins with a 3 digit numeric code. The first digit of the response broadly indicates the success, failure, or progress of the previous command and the second digit indicates the function.
We assigned TCP Port 8150 for this protocol and all the transaction to copyright server is defined in this protocol.
3.3 Components and Operational Flow
Copyright policy management system is composed of three components. Functions of each component and operational flow in this system are described as following.- Copyright Policy Builder
Copyright Policy Builder is a GUI based user interface to assist copyright holders to describe copyright policy in CDL. It leads users to create copyright policy data with no contradictions.
Copyright Server
Copyright server receives copyright policy registration and retrieval requests for the object specified with URI. It authenticates copyright holders on registration part. All the transaction are defined in CTP.
Contents Server
Contents server is a server distributing contents, such as HTTP server, FTP server.
Figure3 : Copyright Policy Management System
4. Design of Policy Enforcement System
Policy Enforcement System provides a mechanism to control content usage based on copyright policy and user capability. In this section, model, functions and operational flow of this system are explained.4.1 Model
Policy Enforcement System can be modeled following the manner of the AAA authorization model [1] in Figure4.
Figure4: Model of Policy Enforcement System
The userfs PC corresponds to the gService Providerh in the AAA authorization model. The mechanism for displaying the media content and providing it to the user, a browser program for example, corresponds to the gService Equipmenth in that same model. The PEE corresponds to the gAAA serverh, which is queried by the gService Equipmenth for whether or not the content can be displayed. Capability Checker, which checks the user rights, corresponds to the User Home Organization (UHO) AAA server in the model.
There are two kinds of broker. One is positioned between the content provider and the capability checker (broker-a) and the other is between the user and the capability checker (broker-b).
Broker-a certifies the userfs rights with respect to the content
independently of user personal authentication and issues a
gcapabilityh that specifies those rights. Examples of broker-a are
the following.
- The content provider itself or an agent of the content provider
- The content marketer
Broker-p is concerned with personal authentication or group
authorization of users. Examples for broker-p are the following.
- Third-party organizations that issue licenses, student identification, credentials, etc. to users
- General certification authorities (CA), which perform personal authentication of users
4.2 Functions
Policy Enforcement System is composed of two components and their functions are as follows.- Policy Enforcement Engine (PEE)
The PEE is a mechanism that interprets copyright policy that is attached to the content and controls its use according to that policy. The copyright policy is described in JAVA language. That is to say, it is a copyright policy program. This engine is equipped with a JAVA interpreter for executing the copyright policy program and provides basic functions for user authorization, checking the rights possessed by the user, decrypting the content, and other functions with respect to the executed copyright policy program.
Capability Checker
The capability checker controls access to the capability database so as to prevent unauthorized copying or forgery of capabilities. Also, rather than simply storing the capability that is received from the broker as it is, it is also possible to record the history of use of the content. Although the system does not currently support digital money, such support is planned for the near future.
4.3 Operation Flow
The operating flow for the case in Figure4 is as follows.- The user create a request to the browser to retrieve the content to be used.
- The browser loads the encrypted content. At the same time, the Copyright Policy Program that is attached to the content is loaded into the PEE.
- The browser queries the PEE for whether or not the content should be displayed.
- The PEE executes the copyright policy program. When required, authorization is requested apability Checker.
- The apability hecker searches the capability database and returns the the PEE.
- The copyright policy program determines whether or the user has the right to access the content. If the user is authorized to use the content, the data that is needed to decrypt the content is returned to the browser.
- The browser displays the media content and provides services for the user.
- The content provider distributes the content to the market (various media such as the Internet or CDROM can be selected).
- The broker issues the capability data and it is registered into Capability database.
5. Implementation
To evaluate this usage control system, we implemented an experimental prototype of this system. In this section, implementation of the prototype is described.5.1 Copyright Policy Builder
Implementation of Copyright Policy Builder is written by Perl as CGI script on the WWW server. Input forms are automatically created to be suitable to the policy inputted in previous forms. At the end, copyright policy data in copyright policy description language is downloaded in text format.5.2 Copyright Server
Copyright Policy Server is implemented in C language and uses Berkley DB 2.7.7 for database. This server implements all commands of the protocol defined in 3.2.This server uses HTTPS server as an interface for registration in order to enable client authentication with X.509 certificates and encryption of communication channel. Copyright policy to be registered should be digitally signed by copyright holders, but in some environments, it may be suitable that copyright policy would be signed by trusted third party. Therefore, this interface is designed to be applicable to both type of registration.
5.3 Policy Enforcement Engine
Currently, this system is implemented entirely in software. As shown in Figure4, a plug-in module has been developed and implemented as a PEE interface for use with Netscape navigator and Real Player. The PEE uses an existing JAVA interpreter and is equipped with a software library that implements the basic functions that are required for executing the policy. This system is implemented on the userfs computerThe capability in the current state of implementation, is an arbitrary character string that is protected by a digital signature.
5.4 Capability Checker
Capability checker is implemented as a Windows system software module that is executed by calls from the PEE. Capability checker and Capability database are implemented on the userfs computer. The capability checker can be implemented through communication over a network. However, it is desirable to implement this function locally on the userfs computer from the viewpoint of protecting userfs privacy, serviceability under off-line.6. Evaluation
For evaluation, we adapted this system to School on the Internet Project which is an online distance education system on the Internet. We selected one course as a sample and evaluate the prototype. This course is composed of 13 video files (RealVideo), 426 image files and 422 html files. We registered copyright policy for all the video and materials of the course. A sample copyright policy and data in CDL are shown in Table1.Table1 : Sample of Copyright Policy and Data in CDL
| -----BEGIN COPYRIGHT POLICY-----
auth1=Jun Murai email1=jun@wide.ad.jp auth2=School on the Internet email2=soi@wide.ad.jp year=1999-2000 type=movie auth_num=2 copy=3 print=1 communicate=3 adapt=2 broadcast=4 change=3 notification=0 auth_type=1,/C=JP/O=School of Internet/ -----END COPYRIGHT POLICY----- |
|
Some of policies such as authentication and notification were achieved and some such as copy(digital) and adaptation were partly limited by encryption. However, we have a lot of limitations because of software limitation as well as characteristics of rights. In this case, compelling users to agree to copyright policy will give some legal obligation to them.
For authentication of students, we built Certification Authority(CA) and issued certificates to students. The subject is C=JP, O=School of Internet, OU=Student. For verification of c
As a result of this experiment, data amount of each material in this system was approximately estimated one and half times as big as the original. This is because of encryption and copyright policy data amount. Table2 shows the estimation of data amount of videos, images and html files.
Table2 : Estimation of data amount
| # of files | total size(plain) | total size(encrypted & attached policy data) | |
| video | 13 | 793Mbyte | 1190Mbyte |
| image | 426 | 6.6Mbyte | 10Mbyte |
| html | 422 | 0.5Mbyte | 0.9Mbyte |
This result is supposed to be scalable from the viewpoint of disc space. Measurement of traffic on the Internet is remained as future work.
7. Conclusion
In order to achieve an environment where every contents on the Internet is appropriately managed, we proposed a usage control system based on copyright. We designed "copyright policy management system" and "policy enforcement system" and implemented each components.This implementation achieved 1)Execution of copyright policy, 2)Expression of copyright policy, 3)Verification of copyright policy, 4) Authorization of users and 5) Protection of contents. These functions achieved reliability and effectiveness of this system. Feasibility is also proved by the result of experiment. We believe this system is a solution of copyright management on the Internet.
However, there are several issues to be discussed and solved in future. Copyright Policy Description Language must be revised to meet various requirements. We are planning to apply our system to other organizations and make qualitative analysis in near future.
Prevention of capability tampering is also necessary. Because
software implementation of tamper resistance is limited, we are
working on partial implementation in hardware. The PEE and capability
checker are implemented as PCMCIA cards that are inserted into the
computer. The capability database is planned to be implemented as a
small card that is inserted into the PCMCIA card. It is assumed that
the user would download the required capability into this card via
internet or by inserting it into an automatic vending machine or a
terminal of a certificate authority.
8. Reference
- J. Vollbrecht, et al. "AAA Authorization Framework", draft-ietf-aaa-authz-arch-00.txt, October 1999
- S. Tashiro, "Capability based resource management scheme for network transferred object", INET'97, July 1997
- K. Okawa, et al. "School of Internet - Building a University on the Internet -", Journal of IPSJ, October 1999
- Y. Murakami, "Copyright information management, A design and implementation of new protocol architecture", INET'99 July 1999