TCP extensions address many issues in the Internet; for example, Multipath TCP achieves efficient utilization of resources of multiple paths, and TcpCrypt opportunistically encrypts all the TCP traffic.
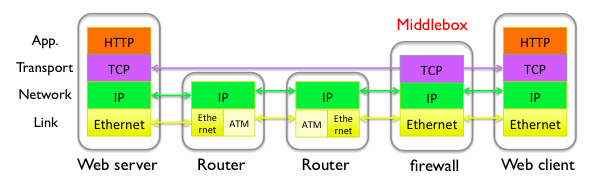
In today's Internet, networks look beyond the IP header for performance optimization and security enhancement. Such elements in the network are called "middleboxes"; firewalls, traffic normalizers and performance-ehnahcing proxies are a few of examples.

Middleboxes, however, prevent TCP extensions from being deployed, thus we must design TCP extensions to conform what middleboxes actually do. However, no one knows that. To address this issue, we are measuring middlebox behaviors relating to TCP extensions. To test as much paths as possible, we'd like you to contribute to this work by running self-contained 1 python script at your available networks. Experiments will finish in approximately 10 -- 15 minutes. This script generates test TCP traffic to a server node, and detects various middlebox behavior, for example, it detects how unknown TCP options are treated and if sequence number is rewritten.
The initial results are available in our paper that appears in ACM Internet Measurement Conference 2011: Is it Still Possible to Extend TCP?"
Out tool generates test TCP traffic by using a raw IP socket or Pcap library. Destinations of the test traffic are port 80, 443 and 34343 on vinson2.sfc.wide.ad.jp located in Japan. The total amount of test traffic is approximately 100 connections (maximum 4 parallel), and each of them uses approximately maximum 2048 bytes. Our experiment doesn't collect traffic information other than those our script generated.
Our script works on Mac OSX 10.5 or 10.6, Linux (kernel 2.6) and FreeBSD (7.0 or higher). This also requires python 2.5 or higher, and libpcap
NOTE for Windows users: If you join the experiment in the guest OS on VirtualBOX, please connect the guest OS via not NAT but bridge. If you join the experiment in the guest OS on VMWare, it does not matter.
1. Download script from http://web.sfc.wide.ad.jp/~micchie/middlebox/for_distrib.tar.gz, and extract to anywhere you like:
% tar xzf for_distrib.tar.gz
2. Execute script by root in the for_distrib directry:
% sudo python run-all.py
After the experiment, you will find a log file (logxxxxxxxxx.tar.gz) in the same directory you executed the script. Please submit this log file, and answer some questions from the submission form. You will see summary of test results in your network after submission (e.g., whether your network passes unknown TCP options).
Or please send the log file to us (micchie at sfc.wide.ad.jp) and tell me your network information as much as you know (e.g., product name of the broadband router, ISP name, product name of firewall appliance etc...) We will tell you summary of the network you tested. In addition, let us know if you have hesitation to open these information.